Email is the easiest medium for malicious attackers to target. Today, more than 90% of targeted Threats enter your Organization through Emails.
The main difference between a common phishing email and a spear phishing email is that the common phishing email mimics a trusted organization and sends an email that requires the victim to log in into the account to collect data, while the latter is more targeted and personalized. Think of it as a custom-made attack that looks not only realistic but also is one on one, “person to person” email. Such an attack can be an email that appears to be sent from a person like a CEO to an employee (of target organization) making it very believable.
It becomes essential for these more dangerous spear phishing emails to be detected and blocked by the cybersecurity measures in place. But what makes this difficult is that the more personalized and sophisticated a phishing email, the harder it is to differentiate the real from the malicious.
At a Glance
What is the incentive for DMARC?
Domain-based Message Authentication Reporting & Compliance is a Sender Policy Framework (SPF) based protocol that works hand in glove with the Domain Key Identified Mail (DKIM) protocol to determine authenticity of an email. With businesses pouring efforts into growing their mailing lists and newsletter subscriber, it is a given that a lot of email traffic is generated between organizations and their customers. Hackers are always looking for a way to inject themselves in this back and forth correspondence.
Domain Spoofing
This is carried out by sending emails with false domain names which look authentic on the surface. Spoof emails are structured skilfully to mimic the styling and branding of a legitimate enterprise or business. The end-goal is to make receivers of the email feel comfortable clicking on the links/attachments in the email.
Spoofers typically forge email headers so that the message appears to originate from a proxy source.
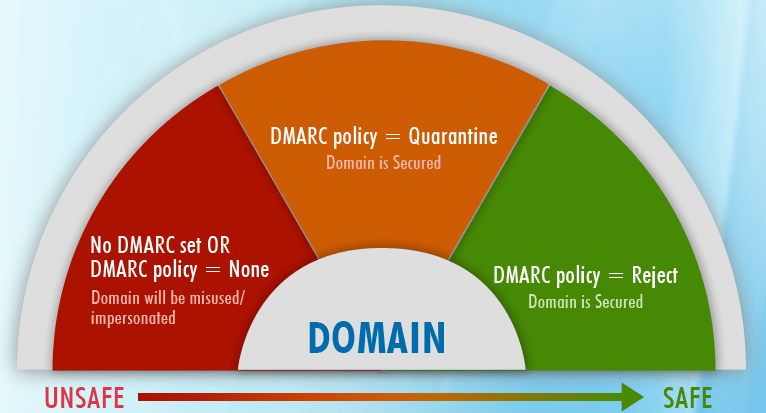
How can DMARC prevent Domain Spoofing?
SPF protocol works on the basis of an IP address, whereas DKIM works on a combination of public-private keys. DMARC attempts to integrate the benefits of both these protocols in order to work efficiently on the domains found in the email headers. DMARC can then describe how feedback can be sent to the domain owners which details how the domain is used across the world wide web.
Logix’s DMARC Monitor is a DMARC compliance tool that accepts reports in the form of XML files from the recipient’s servers. After a thorough analysis, our tool can detect if the domain in consideration is being misused anywhere. Additionally, the DMARC Monitor will help the domain owner correctly deploy SPF and DKIM across all their mailboxes to enforce maximum security.
Protecting your emails is a way to protect your network and your business from spammers and malicious attackers. This is a global necessity for every organization as well as for individuals. As one of the leading IT companies that delivers Email Security from its private cloud Infrastructure, Logix has a core competency in securing over half a million mailboxes.
To know more about DMARC Monitor and how it can help you, visit our website.